In June 2025, cyberattacks disrupted critical government operations in Thomasville, North Carolina, and Georgia’s Ogeechee Judicial Circuit District Attorney’s Office. The attacks forced Thomasville’s city systems offline and caused widespread outages in the DA’s office, which serves four counties. These disruptions led to court closures, phone and internet outages, and severely limited staff capabilities causing significant downtime across municipal services.
While no confirmed data breach has been reported and the exact cause of the attack remains unclear, Georgia officials acknowledged delays in implementing a backup system– highlighting the consequences of not having a fully developed and tested incident response plan.
Here are a few unfortunate facts about cyberattacks:
- Cyberattacks increased by 18% globally in the first quarter of 2025 compared to Q1 2024. (CheckPoint).
- The average cost of a data breach rose to $4.92 million, up from $4.45 million in 2024 (IBM).
- Nearly half of all data breaches are caused by human error, not by hackers breaking through technology layers. (Mechdyne).
Whether your organization operates in government, healthcare, education, manufacturing, or any other sector, cyberattacks are becoming increasingly common. Malicious actors are constantly evolving their tactics to exploit vulnerabilities, leading to the exposure of sensitive client information, prolonged system downtime, financial losses, and a breakdown in client trust. No industry is immune, making cybersecurity a critical priority for all organizations.
While malicious actors are becoming more sophisticated, one of the most effective defenses remains surprisingly simple: preparation. The three key questions every organization must ask are:
- What safeguards do we have in place to prevent an attack?
- How will we respond to an attack when it happens (note we don’t say if, it’s most likely when)
- What is our recovery plan?
In this whitepaper we will discuss: How cyber incidents occur and how an organization can potentially react if an attack occurs.

How Do Cyber Incidents Occur?
Phishing attacks: Phishing attacks are one of the most common tools used, responsible for 31% of all reported breaches and are typically delivered through email. In these attacks, malicious actors impersonate trusted individuals or organizations to trick recipients into clicking on harmful links or sharing sensitive information. These emails often appear legitimate, making it easy for users to unknowingly download malware or disclose personal data such as credit card numbers, Social Security numbers, or login credentials. Phishing can also occur through text messages (smishing) or phone calls (vishing), expanding the threat beyond just email.
Easy to guess passwords: Did you know that malicious actors are now using Artificial Intelligence to crack passwords faster than ever before? Through brute force attacks, AI tools can guess weak passwords in seconds. In fact, a recent study found that 51% of passwords were cracked in under one minute, and 71% within a single day. This highlights the urgent need for strong, complex passwords backed by token-based multi-factor authentication.
Try a few sample passwords here to see how long they would hold up against an attacker.
Exposed information: Sometimes, the biggest cybersecurity risk isn’t a hacker—it’s human error. One common example is writing down passwords on sticky notes, notebooks, or scraps of paper for convenience. While it may seem harmless, this practice leaves sensitive information exposed and vulnerable to theft, especially in shared or public workspaces. In fact, a recent survey found that 35.7% of people still write down their passwords on paper. These seemingly small habits can lead to major consequences, from unauthorized access to full-scale data breaches. Password managers such as LastPass and BitWarden are great tools to use in order to keep your passwords safe.

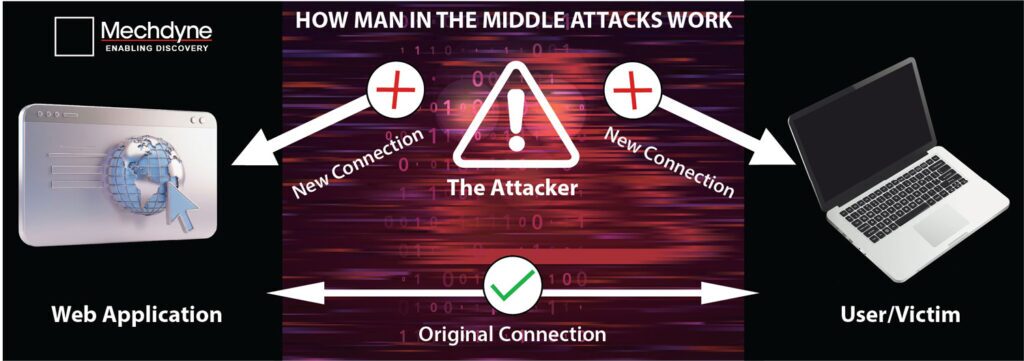
Man-in-the-middle attacks (MitM): A malicious actor secretly intercepts and possibly alters the communication between two parties who believe they are directly communicating with each other. In this scenario, the attacker positions themselves between the sender and the receiver, where they are “sitting in the middle” of the data exchange. This allows them to eavesdrop on the conversation, steal sensitive information, or manipulate the data being transmitted without either party realizing it. Common examples of MitM attacks include fake Wi-Fi hotspots that capture users’ data, email hijacking where attackers intercept and alter email communications, and HTTPS spoofing where a malicious website mimics a secure one to deceive users. These attacks are particularly dangerous because they can compromise personal, financial, or corporate data, often without leaving obvious signs of intrusion. Be wary of emails asking for sensitive information and avoid public Wi-Fi for sensitive transactions.
Zero-Day Vulnerability: A zero-day vulnerability is a security flaw in software or hardware that is unknown to the vendor and has not yet been patched. These vulnerabilities often exist in outdated or unpatched systems. Because the organization is unaware of the flaw, attackers can exploit it before a fix is available, making it a prime target for cyberattacks. There are consequences in ignoring patches and updates. Ensure that your systems are up-to-date.
Insider Threats: Not all cyber incidents come from the outside. Insider threats involve employees, partners, or contractors who accidently or intentionally compromise security. According to a study, insider threats account for over 30% of all data breaches. Whether malicious or negligent, insiders often have access to sensitive systems, making their actions especially dangerous.
How an Organization Can React to a Cyber Incident
While proactive safeguards, like using complex passwords, storing them in a password manager, phishing training for employees, avoiding suspicious links, a thorough offboarding process, and having an incident response plan are essential, they’re not always enough. Cyber attackers are constantly evolving, finding new ways to bypass even the best defenses.
That’s why it’s critical to ask yourself:
- Are we truly prepared if an attack happens today?
- Do we have the right steps in place?
- Is our team ready to respond quickly and effectively?
So, what safeguards should you put in place for your organization?
No matter your current setup, whether you have an internal IT team, work with a managed service provider (MSP), or a combination of both, being prepared to respond to a cyber incident is critical.
Here are five key steps every organization should be ready to take:
1: Detection & Identification
Use security tools such as Intrusion Detection Systems (IDS) and antivirus platforms to continuously monitor your environment for unusual activity, suspicious behavior, or system alerts. These tools help identify potential threats early, allowing your team to respond before significant damage occurs.
2: Contain the Threat
Once an incident is identified, isolate affected systems to prevent the spread. This may involve disabling user accounts, disconnecting devices, or blocking malicious IPs.
3: Eradication & Recovery
Remove malware or unauthorized access. Additionally, patch vulnerabilities or update software. Restore systems from clean backups. Notify affected stakeholders or customers if needed.
4: Communicate and Report
Notify leadership and customers immediately. Keep communicating with regular status updates. Clear communication helps manage risk as well as maintain trust.
5: Learn and Strengthen
Conduct a post-incident review to understand what happened, how it was handled, and what can be improved. Update your incident response plan and provide additional training if needed.
Learn more about Incident Response Protocol Training here.
Pro Tip: Whether your organization has a partner or an internal team assisting with safeguarding your IT infrastructure, it’s worth asking:
- Are roles and responsibilities clearly defined?
- Do we have a tested response plan?
- Are we confident in our ability to act quickly?
Even with support in place, the foundation matters.
Before you can respond effectively to a cyber incident, you need to ensure the basics are covered. These core practices not only reduce your risk but also strengthen your ability to recover quickly and confidently.
Preparation starts with the basics. Make sure your organization has:
- Complex, unique passwords for all accounts
- A secure password manager to store credentials
- Regular phishing awareness training for employees
- Policies to avoid suspicious links and attachments (such as email banners)
- A thorough offboarding process to revoke access
- A documented and tested incident response plan
These foundational practices, combined with a clear response strategy, can significantly reduce your risk and improve your ability to recover from an incident.
Are You Prepared? 8 Services That Strengthen Your Cyber Defense Strategy
Preparation is your strongest defense, but it’s most effective when paired with the right tools and expert support.
These services outlined below form a comprehensive foundation for cybersecurity readiness. Each one addresses a specific layer of defense—whether it’s prevention, detection, response, or recovery. But tools alone aren’t enough. True resilience comes from combining these capabilities with a clear incident response plan, ongoing user awareness, and alignment across teams.
A layered endpoint protection strategy helps defend against a wide range of cyber threats. This typically includes:
Traditional Antivirus (AV Defender): Uses signature-based detection to identify known threats. Centralized management and compliance reporting make it easier to monitor and maintain protection across devices.
Next-Generation Endpoint Detection & Response (EDR): Employs AI-driven behavioral analysis to detect and respond to suspicious activity in real time. These tools can autonomously isolate compromised devices and contain threats before they spread.
Together, these technologies support early threat detection, device isolation, and rapid containment—key components of a resilient cybersecurity posture.
Patch management is the process of regularly updating operating systems and third-party applications to fix known vulnerabilities. This reduces the risk of exploitation, supports regulatory compliance, and helps maintain system stability. Tools like N-able, Intune, and NinjaOne are often used to automate patch deployment, monitor update status, and ensure consistency across devices. Effective patch management minimizes downtime, protects sensitive data, and contributes to a stronger overall security posture.
Disk encryption helps protect sensitive data by converting it into unreadable code that can only be accessed with proper authentication. Centralized disk encryption allows organizations to enforce consistent security policies across compatible devices. Even if a laptop or workstation is lost or stolen, encrypted drives prevent unauthorized access to the data stored within. Tools like AV Defender can be used to manage encryption settings, monitor compliance, and support recovery efforts in case of device compromise.
DNS filtering enhances cybersecurity by blocking access to malicious websites, phishing domains, and other harmful content before a connection is established. By inspecting and controlling DNS requests, it prevents users from inadvertently reaching unsafe destinations. This protection extends beyond the corporate network, helping secure remote and mobile users. DNS filtering works in tandem with endpoint protection tools to reduce exposure to threats and improve overall network hygiene.
5. 24/7 Security Operations Center (SOC)
24/7 Security Operations Center (SOC) provides continuous monitoring of IT environments to detect and respond to threats in real time. It ingests logs from various sources, applies AI-driven anomaly detection, and alerts security analysts to suspicious activity. Operating around the clock, the SOC ensures that threats are investigated and contained, even outside of business hours, helping organizations maintain a strong security posture and minimize response time.
Encrypted cloud backup protects data by securely storing copies of endpoints and servers in offsite locations. Encryption ensures that backup files remain inaccessible to unauthorized users, even if intercepted. These backups support flexible restore options and rapid recovery through local replication, helping organizations minimize downtime and data loss after incidents such as ransomware attacks, hardware failure, or accidental deletion. Maintaining clean, isolated backups is a key component of a resilient disaster recovery strategy.
7. Microsoft 365 Data Protection
Microsoft 365 data protection involves backing up key collaboration tools such as Exchange, OneDrive, SharePoint, and Teams using encrypted, immutable storage. These backups safeguard data against ransomware, accidental deletion, and corruption. Granular recovery options allow organizations to restore individual files, emails, or entire environments, helping maintain productivity and data integrity across the Microsoft ecosystem.
8. Identity & Access Management Support
Identity and access management (IAM) support involves administering platforms like Okta and Azure My Apps to control user access to systems and data. This includes managing access tiles, security groups, and user lifecycle events such as onboarding, role changes, and offboarding. Effective IAM helps ensure that only authorized users can access sensitive resources, reducing the risk of insider threats and enabling swift access changes following security incidents.
Overall cybersecurity is a critical concern for organizations across all industries. As threats continue to evolve in complexity and frequency, the ability to respond effectively is no longer optional—it is essential. Establishing strong foundational safeguards, maintaining a clear and tested incident response plan, and ensuring all stakeholders understand their roles are key components of a resilient cybersecurity strategy.
Preparation is your strongest defense.
Make sure your team, tools, and security plan are in place. Are you truly prepared?
Our experts are available if you’d like to talk through your strategy.


